I’m using Supermicro boards (X11SBA-F) for virtually all of my servers, including the firewall. These boards come with IPMI enabled. The IPMI default configuration vulnerability I’m going to describe here rears its ugly head in dual-homed machines and machines plugged directly to WAN, putting them specifically in great danger.
IPMI is an Intel’s management interface that basically runs an entire separate machine inside your motherboard, allowing you to control virtually all of its functions. You can soft reboot, hard reboot, shutdown or power on the machine (yes, IPMI runs even if the machine is powered off), KVM into the machine and capture and control its console. A user with admin privileges has really a god-like level access.
IPMI is accessed via a LAN interface. And this is where the trouble starts. Which network interface on the multi-homed board such as X11SBA-F/LN4F?
Well, unfortunately for solution security, it’s complicated. Supermicro boards come with three modes of IPMI connectivity:
- Dedicated
- Shared
- Failover (which is a factory default!)
Dedicated mode uses a dedicated IPMI LAN port for IPMI interface. If it’s disconnected you don’t have IPMI access and nobody does.
Shared mode bridges LAN1 with IPMI LAN (essentially creating two network cards with two MAC addresses on one physical port).
Failover mode, which is default, tries the Dedicated mode first and then switches to Shared if the IPMI LAN port is not connected.
By default whichever IPMI port is chosen, the IPMI tries to obtain an address via DHCP.
The default configuration looks like this:
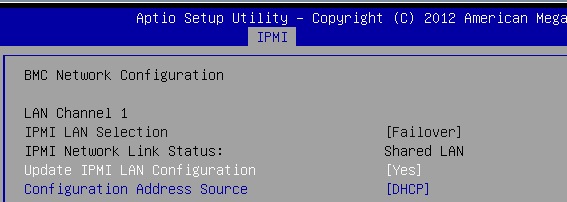
As you may notice above, the IPMI LAN Selection and IPMI Network Link Status settings cannot be changed via BIOS. They are read-only. These settings can only be changed via IPMI itself.
Finally, the default credentials to access IPMI with administrative privileges on Supermicro boards are ADMIN/ADMIN. Neat, huh?
By now you’ve probably already guessed what happens:
- The firewall is built.
- WAN is plugged into LAN1, dedicated IPMI LAN is unplugged.
- Firewall starts up.
- LAN1, used for WAN, obtains a public IP via DHCP from the modem.
- IPMI LAN1 (Failover mode switching to Shared), obtains a public IP via DHCP from the modem.
- IPMI sits open to the whole world with a public IP you don’t know about and no firewall on port 80 with default credentials ADMIN/ADMIN.
Given that I took no steps to enable IPMI and no steps to secure it (as I wasn’t using it until today and had all dedicated ports unplugged on all the servers), I predict there are thousands of machines out there with root hardware access open to the whole world on port 80. If the issue is not isolated to Supermicro boards, I suspect the number may be in hundreds of thousands.
To fix this default configuration vulnerability, the board manufacturers need to do one thing and one thing only and that is to switch Failover IPMI LAN configuration to Dedicated by default. This would require an affirmative action on behalf of the user to enable IPMI access. With current defaults the consequences may be dire.
You’ve been warned.
